
The Presentation of Self on Everyday Internet
Recently, I visited John Lewis and with the aid of a personal stylist went through my first ever wardrobe refresh. The result of this — other than leaving the store overburdened with bags containing shirts, trousers, and shoes, and underburdened in my wallet — had two functions: To finally rid myself of my old stockpile of twenty year old t-shirts and jeans, and to allow me to present myself in new manners.
The value of these new outfits goes beyond mere aesthetics. There are, frustrating as it may be, people out there that will take you more seriously in a powder blue button up than a 24 year old Clerks t-shirt. Sometimes you have to play the game.
Everyday Life
Presentation matters so much in fact that one of my most thumbed-through books is the fantastic Presentation of Self in Everyday Life, by Erving Goffman. Goffman illustrates his points throughout with a full cast of interesting characters that add fascinating colour.
It must be mentioned early that Goffman was not a “man of our times”, and the book was originally published in the 1950s. While I won’t say outright that he was racist, misogynist, or bigoted, the language in the book is challenging to those of us born to a world where thankfully, society has moved forward. If you purchase and read the book, please look past his poor use of language in some phrases, to the ideas the words evoke. He was a superb sociologist, and that’s what we should focus on – taking with us the good, and leaving behind those things that deserve to be left behind.
Goffman

Goffman was a sociologist. His book highlights two of the core social complexities of navigating the world: A person’s appearance, behaviour, and mannerisms (a “presentation”) around different audiences and in different settings; and what cues people take from the observation of these presentations.
Obviously writing at a time before the internet existed he only ever meant for his work to be applied to physical, social spaces. It may seem strange to relate what he says to virtual, hypersocial online spaces.
I’m going to do it anyway.
Presentation and audience
Goffman sees individuals as performers, and those attempting to manage the presentation of themselves or others directors. Those observing them are their audience. If it’s not too cliché to say, to Goffman, all the world is indeed a stage, where more skilled performers carefully curate their presentations to manipulate those around them. Through their presentation, an individual gives off both explicit and implicit signals to those in their presence.
“In the end, our conception of our role becomes second nature and an integral part of our personality. We come into the world as individuals, achieve character, and become persons.”
Robert Ezra Park, Race and Culture
A choice to dress in a certain manner, or to drop or imitate an accent among a certain group of people. The arrival at a meeting a number of minutes early, notepad laid out and sat straight-backed, or drifting in moments after its official start time, coffee in hand. Each choice impacts not only our own engagement, but the perception of all other participants.

Many aspects of these presentations are choices, but sometimes choices are made for us, such as work uniforms or adherence to structured days. In these circumstances, it’s not just an individual’s presentations that matter, but their presentation in relation to the group as a whole.
Presentations also evolve over time in response to the audience’s reaction and the performer’s desires. Either to elicit a different manipulation upon the next impression, or to discover presentations of themselves in which they feel most comfortable. An almost trial and error approach of presentation refinement, using certain audiences as guinea pigs and others as the ‘real deal’. Children, and especially teenagers, are adept at using this aspect of impression management as a means to discover more about who they are, and who they wish to become.
Further still, everyone has a multitude of presentations that they switch between. Someone’s public presentation is likely different from how they present at home, behind closed doors – I don’t speak to my boss the same way I speak to my wife.
Sticking to his acting metaphor, Goffman distinguishes these as frontstage and backstage.
Setting and region
Goffman talks about the setting of a performance throughout the book, but it’s the section on regions and region behaviour that discusses explicitly the bounded nature of perception. In the frontstage one performance is maintained, while in the backstage a more relaxed, perhaps more natural presentation comes through.
A clear example can be seen in a restaurant – a waiter in front of house acts differently before their guests than they may in the kitchen, and differently again in a private office.
Entire demeanours change simply by passing through a threshold that differentiates two rooms, even centimetres apart. A person is able to drop one presentation and pick up another instantly and likely without giving it much, if any, explicit thought.
Identity Impression Management
“The members of the audience may discover a fundamental democracy that is usually well hidden. Whether the character that is being presented is sober or carefree, of high station or low, the individual who performs the character will be seen for what he largely is, a solitary player involved in a harried concern for his production.”
Erving Goffman, The Presentation of Self in Everyday Life
In the section the arts of impression management, Goffman discusses the effort the performer goes to in order to maintain their presentations. This is the work of the directors. A director may be external from the performer — such as the manager of a team — or the performer themselves.
For some presentations this will come naturally, requiring little to no thought at all. You may even consider a presentation that requires no effort whatsoever to be as close to your “true self” as a presentation is able to get. But, a presentation it remains.
In other cases, presentation management takes significant conscious effort. A compulsive liar, who builds up their stories to an extent that it takes a parliamentary privileges committee to bring them crashing back to ground, has to continually recollect the mountain of tales that have led them to any particular moment. One slip up, and the presentation itself collapses, and another beneath it clear to see.
Worse perhaps still, is the risk of multiple presentations clashing in to one another. In different social and professional circles, and regions, different presentations are maintained. An observer familiar with only one presentation may suddenly unearth aspects of an individual’s personality of which they were previously unaware, either by coincidence or neglect on the performer’s part.
The consequences of poor impression management, of dropping a presentation at an inopportune moment, or of having secret presentations exposed vary wildly. From minor annoyance or temporary embarrassment, to a catastrophic destruction of reputation.
Regardless of position, no-one is safe from its terrifying implications. One only has to remember the CEO campfire horror story of Gerald Ratner.
Presentation matters, and management of presentations matters more. The more presentations one maintains, the greater the challenge.
Everyday Internet
Each time we fill in a registration form… we are in essence generating a new persona. A new presentation of ourselves that is visible to an audience, and bounded by the region in which that account can act.
In using Goffman’s language I’ve so far referred to the way that an individual presents themselves and is in turn perceived by others as a presentation. When referring to virtual, online presentations I’ll use the term persona.[1]
Each time we fill in a registration form, each time we install a new client that communicates with others, or generate a new account or character, we are in essence generating a new persona. A new presentation of ourselves that is visible to an audience, and bounded by the region in which that account can act.
Likewise, each time we interact with another through text or avatar, we’re forming a part of the audience of their persona.
“At the heart of digital identities is the concept of the core identity of an individual, which inalienably belongs to that individual. The core identity serves as the quantum from which emerges other forms of digitally derived identities (called personas), which are practically useful and are legally enforced in digital transactions.”
Alex Pentland, David L. Shrier, Thomas Hardjono, and Irving Wladawsky-Berger, Trusted Data – A New Framework for Identity and Data Sharing
Corporate and personal personas
There are two broad categories of interaction we have online: Corporate, and personal. The variety of, and the way we control personas within those categories differs greatly.
Corporate
Corporate interactions, with services and companies, whether through automated systems or their representatives.
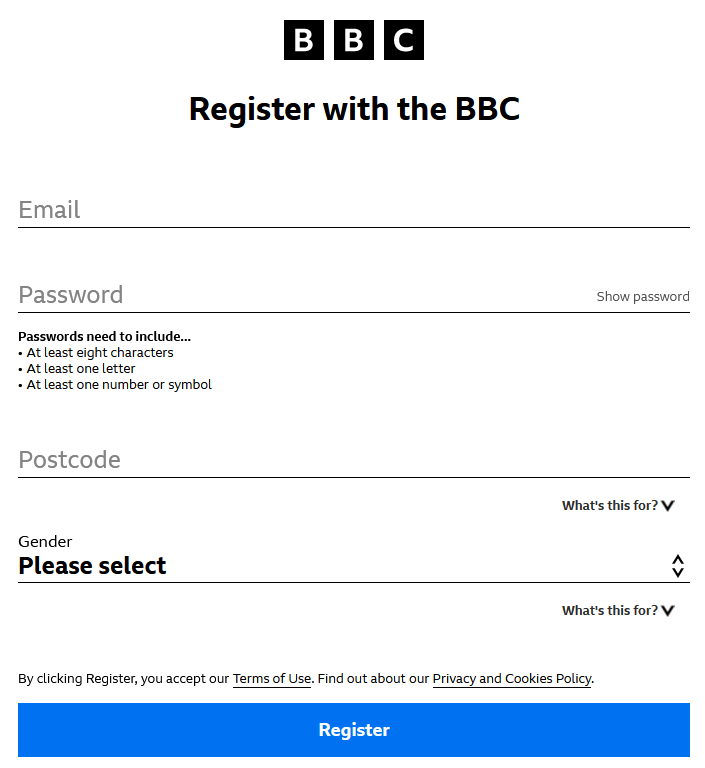
In these relationships our personas are rarely updated. They are generated during registration and vary throughout our relationship with the service either as a reflection of our use of it, or through formal notification – e.g. by changing information on an account profile page.
An individual’s digital corporate personas are heavily constrained. Much more so than in everyday life. Our corporate personas are less based on our mannerisms or aesthetics, but on the set of data that we as individuals choose to grant the service about ourselves. Much like our presentations, we’re often able to lie to a service through our persona in order to manipulate it.
If age is a required field in a registration form, and the input interface for that is a text field, the choice is left to the user what value they enter. The same is true for any non-verified account information. This grants us the ability to be pseudonymous or anonymous. It can also severely limit the value of the data gathered by the service.
Users may only feel required to be truthful about aspects that they think are necessary to access a service’s functionality (if any), such as payment information. Otherwise, they may withhold the truthful nature of any other claims, whether through desire or necessity.
Personal
Personal interactions, directly with other folks on social media sites, forums, inside games, on chat or dating applications.
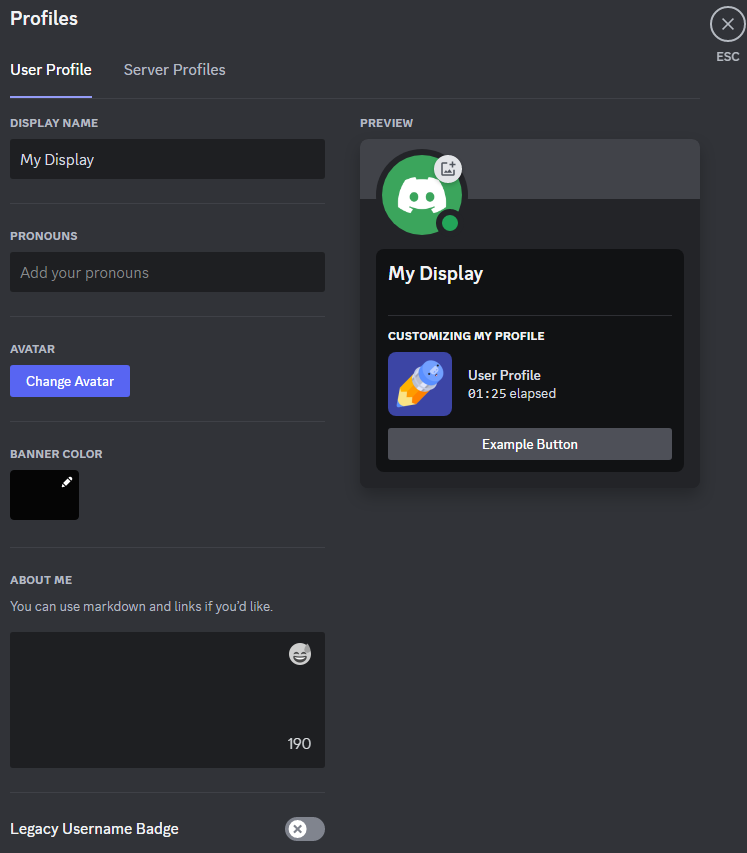
Here, our personas are much more fluid, and rely on interaction as well as static account pages to inform us about the persona of the individual. There’s often little to be gained from reading someone’s profile information other than a username and perhaps a profile picture. Even in tools such as Discord that provide space for an About me section, it’s rare to find more than a brief sentence, quotation, or link to a music video.
Much more akin to Goffman’s presentations, it’s our interactions with others, and the regions in which we choose to express them, that define our personal personas.
The intersection
Certain services will enable both corporate and personal personas. On such services a single corporate persona is encouraged, while multiple personal personas may be permissible. Consider an online game where the persona presented to the service provider — that of a registered account, proof the user is old enough to play the game, monthly fees, and soforth — is seen as entirely independent to the various characters that user then generates in-game to interact with other players.
Total persona independence
It’s now the case that the online personas we interact with are at growing risk of not being backed by a human at all, but rather an AI.
In Goffman’s book, the self always refers to the same physical entity. The person’s “true” identity, for lack of a better term. Any presentation can, for the most part, be easily correlated as belonging to this same “true” identity, and therefore various other presentations. Online personas allow – and indeed in some spaces encourage – total independence between personas.
This is a subtle difference, because truly behind every computer (at least where there’s a human involved) there remains a physical “self”. However, unlike in the physical world where each presentation is reliant on the same actor to inhabit the presentation at any given moment, in the virtual world each persona can be controlled and presented independently.
Even within the same service, such as in an online gaming environment, I may present myself in entirely different ways when playing different characters, even if those characters inhabit the same virtual world.
Offline, it is impossible for two of my presentations to meet one another and exchange words. Online – at least from the audience’s perspective – it’s trivial. Many scams and malicious actors rely on this fact, creating sock puppet accounts which act to amplify or give credit to an otherwise dismissible interaction.
Operators and synthetic personas

Goffman’s model contains performers, directors and an audience. The virtual world has one more role to define: operators – the human (or thing) behind the persona. Distinct from the director, and even the performer, the operator is a uniquely virtual-world concept.
Personas we interact with are at growing risk of not being backed by a human at all, but rather AIs. In this case, the persona has no human backing, indeed it is a purely synthetic persona.
Multitude of personas
The concern of the management of multiple presentations is amplified to the Nth degree online. In the physical world we may alter between a few presentations depending on circumstance and lifestyle. Online, the potential variety is often magnitudes higher.
The increased anonymity and ability to operate under pseudonymous accounts afforded to us by the decoupling of a physical individual from our online personas allow for this discrepancy. The requirement to register to each service, often without any federation or reuseable identity, encourages it.
Multiple simultaneous personas
Furthermore, it is not possible in the environments that Goffman writes about to present an identity in multiple, potentially contradictory presentations at the same time. In the physical world, when acting through your own body, there will only ever be one you. In the virtual world, it’s as simple as alt-tabbing to a different application, or switching to a different tab. What the persona’s operator is doing is impossible for their audience to tell.
Instant transfer of knowledge
In the physical world the transfer of information between locations takes time. If I learn something in one setting, it takes time for me to travel, prepare my presentation (Goffman’s, not slideware!), and represent that information elsewhere. There’s a lag between consuming information and relaying it through a different presentation.
In purely virtual interactions it is as simple as clicking on a different window. In this way knowledge learned by one persona can be instantly relayed by another.
Challenges And Opportunities
To enable people to use their personas in the complex, multi-faceted ways that they use presentations, digital identity needs to develop a more sophisticated approach towards persona management.
The sun is slowly setting on the username/password, register-at-every-new-service, first stage of digital identity. Social and federated login and passkeys are heralds of the new dawn, and beyond that wallet-based credentials offer bright, new opportunities.
Trust in the humanity of the operator
Not being able to trust the operator of the persona you’re interacting with has significant implications for both our personal and corporate interactions.
Perhaps the greatest challenge that lies ahead in digital identity is that of verifying the authenticity of the humanity of the participants in an interaction. It seems almost inevitable that shortly ChatGPT or similar chatbot AI will emerge capable of passing the Turing Test.
This is further confounded by the emergence of human-like AI-generated avatars for video-calls, and the advances in voice mimicry by AI using only the briefest of samples of an authentic human’s voice.
Not being able to trust the operator of the persona you’re interacting with has significant implications for both our personal and corporate interactions. Research and development around proving your own humanity, and of those you’re interacting with, is an exciting field. Peer-based interactions, progressive disclosure of personas, and reciprocal trust relationships will all have their parts to play.
Trust in the identity of the operator
In personal persona interactions, even if we can trust that we’re interacting with a human, can we really trust that we’re interacting with the same human across repeated interactions? After all, a persona may be controlled by multiple operators.
This isn’t simply a concern around man-in-the-middle attacks, rather our ability to trust an interaction with operators across multiple services.
Impersonation of operators is a frequent technique of scammers and fraudsters. If two services don’t use the same underlying persona via federation or reuseable identity, a requirement exists to establish that the same operator is in control of both personas.
Being able to trust the identity of the operator of a persona comes at an overhead of cautiousness. One that the digital identity industry should work hard to help reduce as much as possible.
Progressive disclosure of personas
In the physical world, it’s commonplace for presentations to shift gradually over time, based on a growing level of familiarity between the interacting performers. Wallet-based credentials have the opportunity to establish analogous interactions for both our personal and corporate personas.

By first making claims about myself in an unverified way, I can establish a connection with another persona. Over time, I can choose to request and present a set of verifiable credentials that back up (or override) the claims I’ve made myself.
It seems fairly likely that a persona may, over time, be considered to be the set of credentials that I choose to present. Representing my work persona, I present a certain set of credentials – proof of employment, professional certificates, membership of various bodies; when playing a video game, I present a different set – a credential of my avatar’s name, a set of its accomplishments, and so forth.
These various personas can be presented all from the same wallet, giving me the choice of to whom I demonstrate a correlation between my personas.
Reciprocal trust relationships
Reciprocity, repeated interaction, explicit and implicit cues, and transference between parties – these are the four components that allow trust between parties to develop.[2]
The progressive disclosure of personas enabled by verifiable wallet-based credentials, in exchange for granting increased access to a service’s offerings helps to address the first three of these components.
The opportunities in this model of interaction between services and their user’s personas create a relationship based on earning and retaining trust.
This reciprocal trust relationship encourages users to interact with a service using a persona that opens up a greater amount of verifiable data when they feel comfortable, and to revoke access to that verifiable data, or replace it with less trustworthy data, should their attitude to the service change. This is especially true if services are instructed to not store credential-based information, and must request it via explicit consent during a process that requires it.
These tit-for-tat relationships between services and users enable the most valuable features of a service to be offered in exchange for more valuable, verified data from a user. Further, by not storing the data, services reduce the value of their data stores as a target of malicious actors. Additionally, they increase the level of trust and choice that a user can establish with them, and ensure explicit consent for use of user data.
Separation of personas
To support reciprocal trust relationships, defensive tooling and techniques should be developed to support users from accidentally revealing personas in regions they don’t wish to expose them.
With personas driven by wallet-based credentials, it would behove wallet vendors to offer simple user experiences in the selection of credentials during presentation, and separation of credentials associated with a given aspect of an individual’s life.
With multiple credentials that indicate my name, I don’t want to be at risk of sharing a gaming avatar’s name from a gaming persona in place of my actual name from a work persona when queried for it in a professional setting.
Reuse of personas
Tooling should also encourage the reuse of personas across multiple appropriate and related settings – reducing the multitude of personas to a manageable set. This benefits the user – they have fewer overall personas to manage. It also benefits the user’s audience – by keeping the data they are presented with up to date.
Maintaining a strict division between my gaming and work personas is important. However, the reuse of my various gaming personas across multiple gaming services enables me to rapidly bootstrap into a new game, helping me locate my friends and bringing my accomplishments with me.
By reusing my professional personas as I change jobs, and presenting those to various standards bodies I interact with, I only need to alter my personas by updating the set of credentials that form them once. Rather than update each service’s static data, I update the much smaller set of personas, and then choose to present the appropriate one, at the time of my interaction with that service.
Closing Thoughts
It’s time to start accepting and encouraging users to present themselves as they choose, through their own dynamic personas, as they do with their presentations in the physical world.
Digital personas, as with offline presentations, are an inevitable part of our interactions on the internet. To allow us the flexibility and control of our personas comparative to presentations, digital identity must evolve.
In addition to Goffman’s performers, audiences, and directors, the virtual world brings a new role in operators, and new prospects and threats through synthetic personas.
Tooling to aid in the separation and reuse of personas, and to enable the progressive disclosure of persona information within a setting will help users manage their personas in a similar way to how physical presentations are separated by regions, and change based on their audience.
Digital services and interactions often occur with our digital identities at too high a level – an entire identity, or too low a level – individual claims within those identities. They gather this data not giving a choice to the user about whether to make a claim to its veracity, and store it in a static form. It’s time to start accepting and encouraging users to present themselves as they choose, through their own dynamic personas, as they do with their presentations in the physical world.
This introduces new challenges and opportunities, primarily for humans to present themselves online in as varied ways as we can in the physical world, but also in defending our human interactions against the increasing risks of AI in the field of digital identity.
References
[1] Trusted Data: A New Framework for Identity and Data Sharing
Part I, Section 2, Towards and Internet of Trusted Data, Alex Pentland, David L. Shrier, Thomas Hardjono, and Irving Wladawsky-Berger
[2] Privacy as Trust, Information Privacy for an Information Age
Part II, Section 4, Trust and Sharing, Ari Ezra Waldman
Some images in this piece generated by Bing Image Creator